By default Windows Server 2016 sets external remote desktop access to disabled as a security measure, we can easily optionally enable it from within the server console to everyone or a. Clients without a proper certificate from your own PKI infrastructure, that runs by default on a Windows Server 2016 Essentials, cannot connect to Direct Access. Deploying Direct Access on a server that runs the ‘Essentials Experience’ role on a Windows Server 2016 Standard/Datacenter or on a Windows Server Essentials 2016 SKU requires more.
-->Applies To: Windows Server (Semi-Annual Channel), Windows Server 2016, Windows Server 2012 R2, Windows 10
The Remote Access guide provides you with an overview of the Remote Access server role in Windows Server 2016, and covers the following subjects:
For more information about other networking technologies, see Networking in Windows Server 2016.
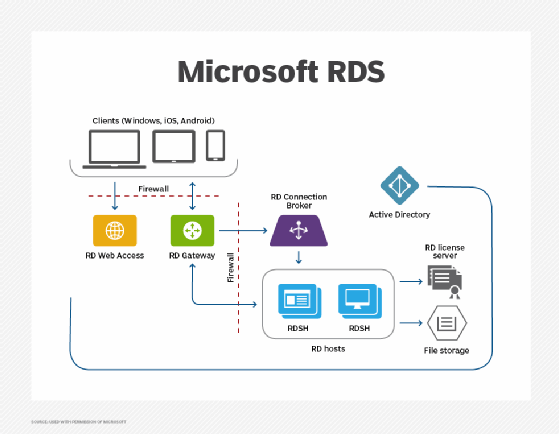
The Remote Access server role is a logical grouping of these related network access technologies: Remote Access Service (RAS), Routing, and Web Application Proxy. These technologies are the role services of the Remote Access server role. When you install the Remote Access server role with the Add Roles and Features Wizard or Windows PowerShell, you can install one or more of these three role services.
Important
Do not attempt to deploy Remote Access on a virtual machine (VM) in Microsoft Azure. Using Remote Access in Microsoft Azure is not supported. You cannot use Remote Access in an Azure VM to deploy VPN, DirectAccess, or any other Remote Access feature in Windows Server 2016 or earlier versions of Windows Server. For more information, see Microsoft server software support for Microsoft Azure virtual machines.

Remote Access Service (RAS) - RAS Gateway
When you install the DirectAccess and VPN (RAS) role service, you are deploying the Remote Access Service Gateway (RAS Gateway). You can deploy the RAS Gateway a single tenant RAS Gateway virtual private network (VPN) server, a multitenant RAS Gateway VPN server, and as a DirectAccess server.
RAS Gateway - Single Tenant. By using RAS Gateway, you can deploy VPN connections to provide end users with remote access to your organization's network and resources. If your clients are running Windows 10, you can deploy Always On VPN, which maintains a persistent connection between clients and your organization network whenever remote computers are connected to the Internet. With RAS Gateway, you can also create a site-to-site VPN connection between two servers at different locations, such as between your primary office and a branch office, and use Network Address Translation (NAT) so that users inside the network can access external resources, such as the Internet. In addition, RAS Gateway supports Border Gateway Protocol (BGP), which provides dynamic routing services when your remote office locations also have edge gateways that support BGP.
RAS Gateway - Multitenant. You can deploy RAS Gateway as a multitenant, software-based edge gateway and router when you are using Hyper-V Network Virtualization or you have VM networks deployed with virtual Local Area Networks (VLANs). With the RAS Gateway, Cloud Service Providers (CSPs) and Enterprises can enable datacenter and cloud network traffic routing between virtual and physical networks, including the Internet. With the RAS Gateway, your tenants can use point-so-site VPN connections to access their VM network resources in the datacenter from anywhere. You can also provide tenants with site-to-site VPN connections between their remote sites and your CSP datacenter. In addition, you can configure the RAS Gateway with BGP for dynamic routing, and you can enable Network Address Translation (NAT) to provide Internet access for VMs on VM networks.
Important
The RAS Gateway with multitenant capabilities is also available in Windows Server 2012 R2.
- Always On VPN. Always On VPN enables remote users to securely access shared resources, intranet Web sites, and applications on an internal network without connecting to a VPN.
For more information, see RAS Gateway and Border Gateway Protocol (BGP).
Routing
You can use Remote Access to route network traffic between subnets on your Local Area Network. Routing provides support for Network Address Translation (NAT) routers, LAN routers running BGP, Routing Information Protocol (RIP), and multicast-capable routers using Internet Group Management Protocol (IGMP). As a full-featured router, you can deploy RAS on either a server computer or as a virtual machine (VM) on a computer that is running Hyper-V.
To install Remote Access as a LAN router, either use the Add Roles and Features Wizard in Server Manager and select the Remote Access server role and the Routing role service; or type the following command at a Windows PowerShell prompt, and then press ENTER.
Web Application Proxy
Web Application Proxy is a Remote Access role service in Windows Server 2016. Web Application Proxy provides reverse proxy functionality for web applications inside your corporate network to allow users on any device to access them from outside the corporate network. Web Application Proxy pre-authenticates access to web applications using Active Directory Federation Services (AD FS), and also functions as an AD FS proxy.
To install Remote Access as a Web Application Proxy, either use the Add Roles and Features Wizard in Server Manager and select the Remote Access server role and the Web Application Proxy role service; or type the following command at a Windows PowerShell prompt, and then press ENTER.
For more information, see Web Application Proxy.
 -->
-->Applies To: Windows Server (Semi-Annual Channel), Windows Server 2016
This topic describes how to configure the client and server settings that are required for remote management of DirectAccess clients. Before you begin the deployment steps, ensure that you have completed the planning steps that are described in Step 2 Plan the Remote Access Deployment.
| Task | Description |
|---|---|
| Install the Remote Access role | Install the Remote Access role. |
| Configure the deployment type | Configure the deployment type as DirectAccess and VPN, DirectAccess only, or VPN only. |
| Configure DirectAccess clients | Configure the Remote Access server with the security groups that contain DirectAccess clients. |
| Configure the Remote Access server | Configure the Remote Access server settings. |
| Configure the infrastructure servers | Configure the infrastructure servers that are used in the organization. |
| Configure application servers | Configure the application servers to require authentication and encryption. |
| Configuration summary and alternate GPOs | View the Remote Access configuration summary, and modify the GPOs if desired. |

Note
This topic includes sample Windows PowerShell cmdlets that you can use to automate some of the procedures described. For more information, see Using Cmdlets.
Install the Remote Access role
You must install the Remote Access role on a server in your organization that will act as the Remote Access server.
To install the Remote Access role
To install the Remote Access role on DirectAccess servers

On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features.
Click Next three times to get to the server role selection screen.
On the Select Server Roles dialog, select Remote Access, and then click Next.
Click Next three times.
On the Select role services dialog, select DirectAccess and VPN (RAS) and then click Add Features.
Select Routing, select Web Application Proxy, click Add Features, and then click Next.
Click Next, and then click Install.
On the Installation progress dialog, verify that the installation was successful, and then click Close.
Windows PowerShell equivalent commands
The following Windows PowerShell cmdlet or cmdlets perform the same function as the preceding procedure. Enter each cmdlet on a single line, even though they may appear word-wrapped across several lines here because of formatting constraints.
Configure the deployment type
There are three options that you can use to deploy Remote Access from the Remote Access Management console:
DirectAccess and VPN
DirectAccess only
VPN only
Note
This guide uses the DirectAccess only method of deployment in the example procedures.
To configure the deployment type
On the Remote Access server, open the Remote Access Management console: On the Start screen, type, type Remote Access Management Console, and then press ENTER. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
In the Remote Access Management Console, in the middle pane, click Run the Remote Access Setup Wizard.
In the Configure Remote Access dialog box, select DirectAccess and VPN, DirectAccess only, or VPN only.
Configure DirectAccess clients
For a client computer to be provisioned to use DirectAccess, it must belong to the selected security group. After DirectAccess is configured, client computers in the security group are provisioned to receive the DirectAccess Group Policy Objects (GPOs) for remote management.
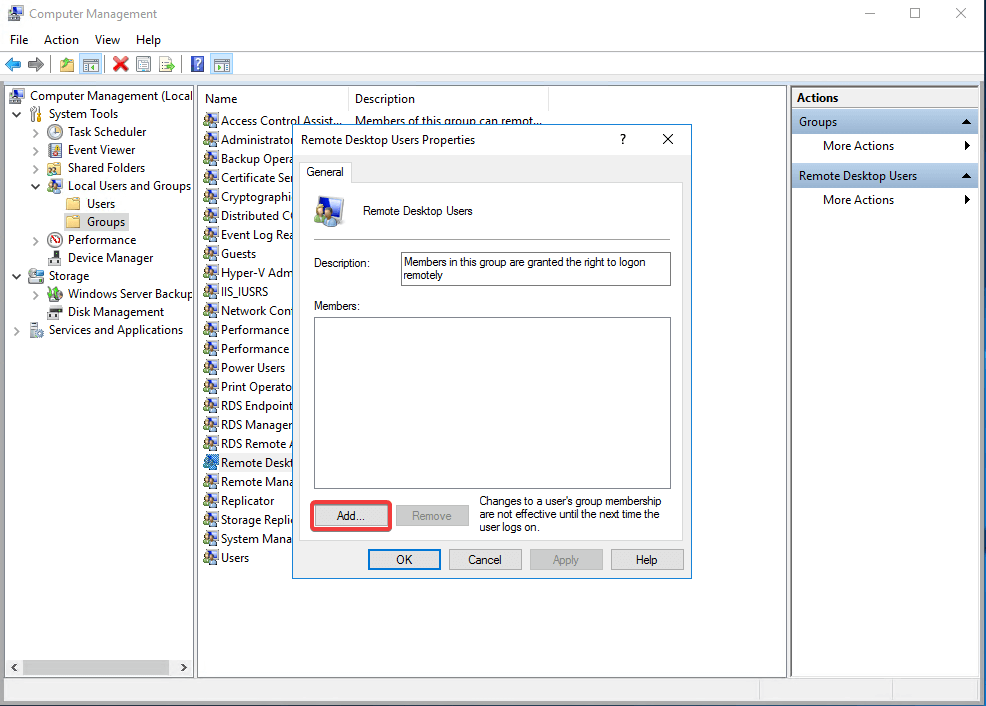
Enable Rdp On Server 2016
To configure DirectAccess clients
In the middle pane of the Remote Access Management console, in the Step 1 Remote Clients area, click Configure.
In the DirectAccess Client Setup Wizard, on the Deployment Scenario page, click Deploy DirectAccess for remote management only, and then click Next.
On the Select Groups page, click Add.
In the Select Groups dialog box, select the security groups that contain the DirectAccess client computers, and then click Next.
On the Network Connectivity Assistant page:
In the table, add the resources that will be used to determine connectivity to the internal network. A default web probe is created automatically if no other resources are configured. When configuring the web probe locations for determining connectivity to the enterprise network, ensure that you have at least one HTTP based probe configured. Configuring only a ping probe is not sufficient, and it could lead to an inaccurate determination of connectivity status. This is because ping is exempted from IPsec. As a result, ping does not ensure that the IPsec tunnels are properly established.
Add a Help Desk email address to allow users to send information if they experience connectivity issues.
Provide a friendly name for the DirectAccess connection.
Select the Allow DirectAccess clients to use local name resolution check box, if required.
Note
When local name resolution is enabled, users who are running the NCA can resolve names by using DNS servers that are configured on the DirectAccess client computer.
Click Finish.
Configure the Remote Access server
To deploy Remote Access, you need to configure the server that will act as the Remote Access server with the following:
Correct network adapters
A public URL for the Remote Access server to which client computers can connect (the ConnectTo address)
An IP-HTTPS certificate with a subject that matches the ConnectTo address
IPv6 settings
Client computer authentication
To configure the Remote Access server
In the middle pane of the Remote Access Management console, in the Step 2 Remote Access Server area, click Configure.
In the Remote Access Server Setup Wizard, on the Network Topology page, click the deployment topology that will be used in your organization. In Type the public name or IPv4 address used by clients to connect to the Remote Access server, enter the public name for the deployment (this name matches the subject name of the IP-HTTPS certificate, for example, edge1.contoso.com), and then click Next.
On the Network Adapters page, the wizard automatically detects:
Network adapters for the networks in your deployment. If the wizard does not detect the correct network adapters, manually select the correct adapters.
IP-HTTPS certificate. This is based on the public name for the deployment that you set during the previous step of the wizard. If the wizard does not detect the correct IP-HTTPS certificate, click Browse to manually select the correct certificate.
Click Next.
On the Prefix Configuration page (this page is only visible if IPv6 is detected in the internal network), the wizard automatically detects the IPv6 settings that are used on the internal network. If your deployment requires additional prefixes, configure the IPv6 prefixes for the internal network, an IPv6 prefix to assign to DirectAccess client computers, and an IPv6 prefix to assign to VPN client computers.
On the Authentication page:
For multisite and two-factor authentication deployments, you must use computer certificate authentication. Select the Use computer certificates check box to use computer certificate authentication and select the IPsec root certificate.
To enable client computers running Windows 7 to connect via DirectAccess, select the Enable Windows 7 client computers to connect via DirectAccess check box. You must also use computer certificate authentication in this type of deployment.
Click Finish.
Configure the infrastructure servers
To configure the infrastructure servers in a Remote Access deployment, you must configure the following:
Network location server
DNS settings, including the DNS suffix search list
Any management servers that are not automatically detected by Remote Access
Windows Server 2016 Remote Access Policy
To configure the infrastructure servers
In the middle pane of the Remote Access Management console, in the Step 3 Infrastructure Servers area, click Configure.
In the Infrastructure Server Setup Wizard, on the Network Location Server page, click the option that corresponds to the location of the network location server in your deployment.
If the network location server is on a remote web server, enter the URL, and then click Validate before you continue.
If the network location server is on the Remote Access server, click Browse to locate the relevant certificate, and then click Next.
On the DNS page, in the table, enter additional name suffixes that will be applied as Name Resolution Policy Table (NRPT) exemptions. Select a local name resolution option, and then click Next.
On the DNS Suffix Search List page, the Remote Access server automatically detects domain suffixes in the deployment. Use the Add and Remove buttons to create the list of domain suffixes that you want to use. To add a new domain suffix, in New Suffix, enter the suffix, and then click Add. Click Next.
On the Management page, add management servers that are not detected automatically, and then click Next. Remote Access automatically adds domain controllers and Configuration Manager servers.
Click Finish.
Configure application servers
In a full Remote Access deployment, configuring application servers is an optional task. In this scenario for remote management of DirectAccess clients, application servers are not utilized and this step is greyed out to indicate that it is not active. Click Finish to apply the configuration.
Configuration summary and alternate GPOs
When the Remote Access configuration is complete, the Remote Access Review is displayed. You can review all of the settings that you previously selected, including:
GPO Settings
The DirectAccess server GPO name and Client GPO name are listed. You can click the Change link next to the GPO Settings heading to modify the GPO settings.
Remote Clients
The DirectAccess client configuration is displayed, including the security group, connectivity verifiers, and DirectAccess connection name.
Remote Access Server
The DirectAccess configuration is displayed, including the public name and address, network adapter configuration, and certificate information.
Infrastructure Servers
This list includes the network location server URL, DNS suffixes that are used by DirectAccess clients, and management server information.
Windows Server 2016 Tutorial
See also
